
12 Questions you should ask when choosing a Managed XDR
Discover the 12 essential questions to ask when selecting a managed XDR solution (MXDR). Make an informed choice for robust threat detection and response.
It is becoming increasingly difficult for cyber security teams to evolve their detection and response capabilities fast enough to defend against the latest threat-actor tactics. More and more organizations are turning to managed detection and response services to boost their internal capabilities. Managed Extended Detection and Response (MXDR) is a fully managed 24/7 MDR service that provides holistic and robust protection against internal and external cyber threats.

“By 2025, 60% of organizations will be actively using remote threat disruption and containment capabilities delivered directly by MDR providers.”
MXDR Primer
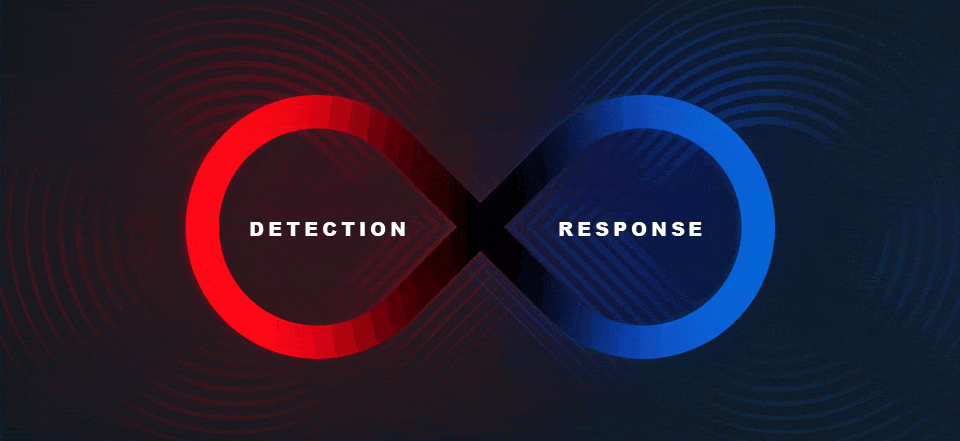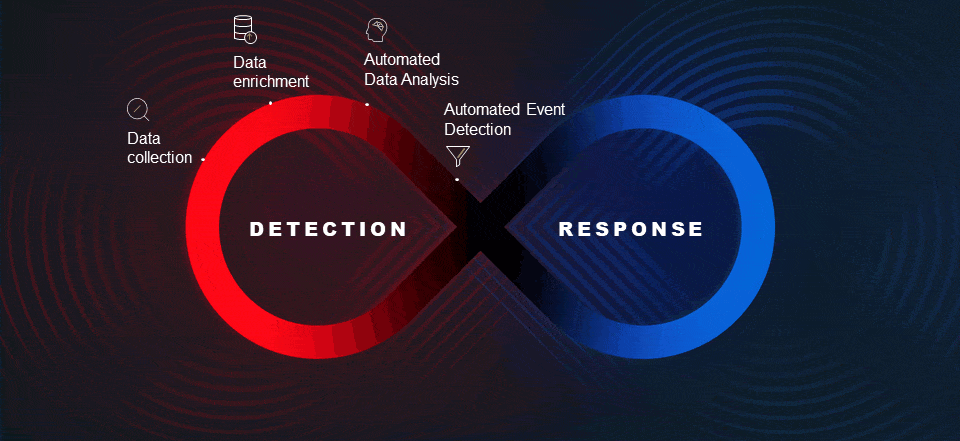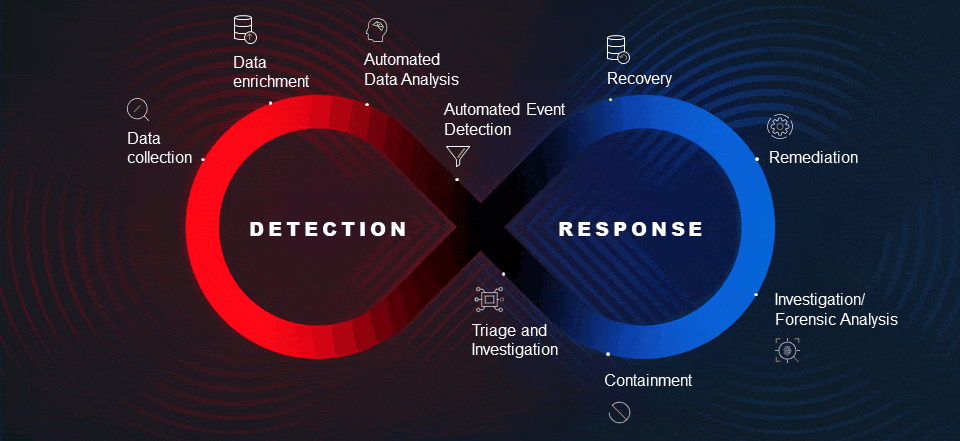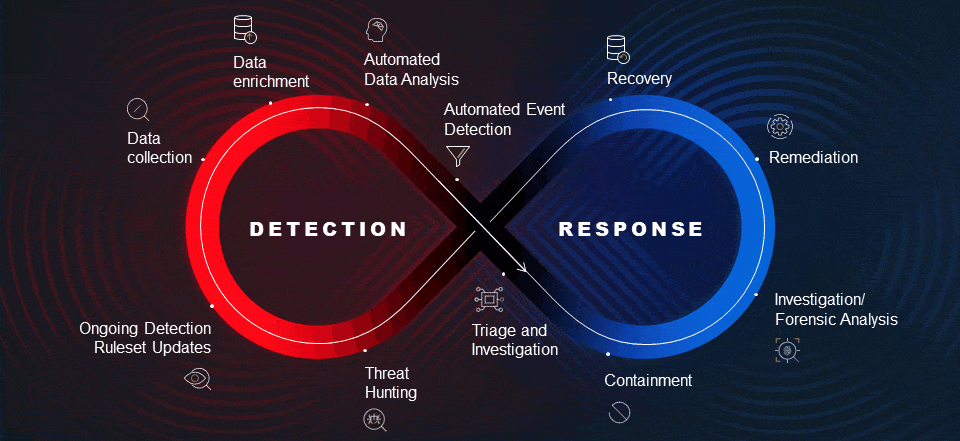
MXDRs are based on XDR platforms that go beyond traditional endpoint detection and response (EDR), by integrating and correlating data from multiple domains, including the endpoints, network edge and core, applications, and identity systems, across both on-premises and cloud environments. An MXDR provides XDR capabilities.
Organizations that are considering deploying an MXDR are faced with a choice between multiple MXDR offerings that are relatively diverse in capabilities, despite being part of the same service class.
What are the questions organizations should be asking when evaluating MXDR services, to make sure they deploy the service that best meets their needs? We’ve assembled a few of key questions below.
1. Will it cover my entire infrastructure…from the outset?
An MXDR intrinsically provides a broader view of the network than an EDR-based detection and response service. Nevertheless, even for an MXDR service, comprehensive network coverage is not a given, because it is dependent on the ability of the associated XDR to integrate with the client’s existing cyber defense systems and IT and OT infrastructure. If the integration and consequent network coverage is only partial, there will be blind spots that an attacker can exploit.
2. Is the MXDR known for its reliability and effectiveness in real-world scenarios?
The best XDRs have been deployed extensively by IR teams to enable a rapid response to a broad range of incidents across a diverse range of industries. The platform demands of IR teams are extensive, and when an IR team is responding to a major incident, time is of the essence. Any XDR they use must be easy to deploy, facilitate triage, and drive containment – all at speed. The XDR needs to provide advanced detection that will preempt attacker reentry attempts, and to provide the advanced forensics and reporting capabilities that IR teams and their clients require. For all of these reasons, IR-bred XDRs are optimal platforms for an MXDR service.

“Effective MDR is powered by effective IR.”
Forrester Research, February 2023
3. Will it eliminate our organization’s event fatigue?
Detection accuracy is paramount. Too many false positives sent to the client by the MXDR team will nullify one of the key reasons most clients adopt MXDRs: elimination of event fatigue. False positives can also raise the odds of missing genuine threats, escalating the risk of a breach. Over-filtering is not a solution, because this can cause real events to be missed. To achieve sufficient decision accuracy, the MXDR needs to monitor the same entity from multiple data sources. For example, to monitor an endpoint in the cloud, the XDR needs to be gathering information from the relevant EDR, identity system, and SIEM.
4. What is the experience level of the MXDR team?
MXDR analysts have a critical role, even when they are supported by advanced, AI-driven detection. The MXDR analysts leverage their experience to add a critical layer of validation and decision-making to threat isolation, triage, containment, and remediation. Analysts need to ensure that any actions taken are totally aligned with the IT policies of the client.
5. Is the MXDR team supported by concentric layers of expertise?
It is important to check to what degree the MXDR team is backed by:
- Incident response
- Adversarial tactics
- Threat hunting
- Enterprise security
- Forensics
- Cloud
- OT
An MXDR team should be able to handle the majority of detected security events itself, but when particular situations arise that require specific domain expertise, internal support teams with the right expertise help ensure that event triage is accurate and the transition from detection to response is swift and effective.
6. Is the latest threat intelligence embedded into the MXDR?
It is important to understand how and to what extent threat intelligence is gathered and infused into the MXDR. Comprehensive threat intelligence is ‘oxygen’ for MXDRs. Gathering quality intelligence involves constantly processing and analyzing data from across the global threat landscape to understand the latest threat-actor tactics, techniques, and procedures (TTPs), and indicators of compromise (IOCs) being used across all key verticals, technologies and regions. MXDR providers that have a large in-house IR practice as well as an internal threat research team have access to the field intelligence that will empower the MXDR with a higher level of detection and response capabilities.
7. When a real event is detected, will we need to find an IR provider ourselves?
Some MXDR providers have experienced IR teams in-house, others do not. The necessity of zero lag time between detecting an event and launching a response mandates that the vendor have an internal IR team to ensure that security incidents are swiftly contained and remediated.
8. What level of experience does the vendor’s in-house IR team have?
If the in-house IR box is ‘checked’, then the level of that team’s expertise needs to be probed. The IR team must be capable and experienced in responding to all types of attacks that could be launched against the client. With an increasing number of attacks being launched by nation-state level threat actors, IR teams with nation-state level cyber warfare experience have the best chance of containing and eradicating these kinds of attacks and facilitating recovery in the shortest possible time.
9. Does the MXDR service include an incident response retainer?
An incident response retainer (IRR) provides a runbook with predetermined critical engagement parameters that will accelerate the response to a cyber incident. IRR discovery sessions include a high-level review of the client’s network and IT architecture, critical systems, secure data sharing, and access processes. An IRR is a natural component of an MXDR deployment and should be considered a mandatory feature of an MXDR service.
10. Will the MXDR integrate with our existing security stack?
The effectiveness of an MXDR solution depends on its ability to integrate seamlessly with a diverse range of pre-existing security tools within an organization’s security stack. ‘Out of the box’ integration capabilities greatly enhance the speed and effectiveness of MXDR deployment. Some vendors will claim neutrality, but at the same time will strongly recommend that the client deploy specific products into their security stack to ensure optimal detection. That is not true vendor-neutrality.
11. Does the MXDR vendor offer a tailored approach?
Organizations operate in distinct contexts with unique threats, specific internal policies, governance processes, and compliance requirements. An MXDR provider must be able to provide a tailored service that will align with the client’s operational context and network topology. A tailored service can include unique detection scenarios for the client’s industry vertical and response playbooks that define the degree of response autonomy.
12. Is AI used to optimize detection and ensure scalability?
The underlying XDR should utilize advanced machine learning or deep learning algorithms to analyze the vast data volumes and detect anomalies, patterns, and potential threat indicators. Additionally, the service should be able to monitor user behavior patterns to detect suspicious behavior – typically using tools such as user and entity behavior analytics (UEBA). AI enables faster detection at scale, improved triage, and a more accurate response.
MXDR Can Be a Cornerstone of Proactive Defense and Business Resilience
Opting for an MXDR can be a strategic leap that enhances an organization’s cybersecurity. By asking the right questions, organizations have a better chance of selecting a vendor that will be a good fit for their business and threat landscape.
Ready to amplify your security operations? Book a Demo to see Sygnia’s Velocity MXDR in action.
Want to learn more? click here.

By clicking Subscribe, I agree to the use of my personal data in accordance with Sygnia Privacy Policy. Sygnia will not sell, trade, lease, or rent your personal data to third parties.
