
NIS2 Readiness
Organizations that are classified as essential or important entities need to start preparing for NIS2 now because it will take time to internally implement the measures that NIS2 mandates.
Summary
- The NIS Directive establishes baseline security requirements and practices for entities with a presence in the EU.
- The goal of NIS2 is to drive a high level of cyber resilience across a wide range of EU organizations and industry verticals.
- In comparison to NIS1, NIS2 enacts:
• Coverage of a much broader range of industries and service sectors
• Toughened enforcement penalties
• Greater C-level accountability
• Stricter and more comprehensive supervisory and reporting requirements - UK organizations need to align with the Cyber Assessment Framework (CAF).
- Organizations in the EU and UK need to start preparing for NIS2 now by performing a comprehensive cyber risk assessment.
160,000+
EU ESTIMATE OF THE # OF COMPANIES AFFECTED BY NIS2
OCTOBER 18, 2024
DATE BY WHICH EU MEMBER STATES MUST BEGIN TO ENFORCE NIS2
Background
The EU Directive on Security of Network and Information Systems (the NIS Directive) establishes security requirements and practices for entities with a presence in the EU. The goal of NIS2 is to drive improved cyber resilience across a wider range of organizations, and to do so in a more comprehensive and consistent way than NIS1. A third goal is to ensure more uniform transposition of the directive into local law across EU member states.
Organizations in the UK need to align with the Cyber Assessment Framework (CAF) which was developed by the UK’s National Cyber Security Centre (NSCS) to support compliance with NIS2.
NIS2 builds on NIS1 and addresses its deficiencies. Organizations need to be aware that NIS2 affects more industry sectors, has stricter supervisory and reporting requirements, and heavier fines for non-compliance. NIS2 has toughened the requirements around cybersecurity enforcement, including new definitions of C-Level accountability. The NIS2 directive seeks to improve cyber resilience of essential and important entities across three key domains of security requirements, each with its own set specific measures that must be followed:

NIS2 Categories and Specific MeasuresEntities impacted by NIS2
NIS2 significantly broadens the list of industry categories that are subject to the directive, and divides those categories into two groups: ‘essential’ and ‘important’. Entities that are defined as essential will be subject to proactive compliance monitoring by regulatory authorities. Entities that are defined as important may be checked for NIS2 compliance in response to the content of a report that the important entity or a related entity filed, or in response to a cyber incident.
EU member states can modify the list of essential and important entities, so an EU organization needs to validate its classification in each country it operates in. However, one of the main goals of NIS2 is to achieve more classification consistency between EU member states, so in theory organizations should be in the same entity class regardless of country.
Below we list the baseline essential and important entities as defined by the EU.
Essential entities
The industry sectors defined as essential by the NIS2 directive are those that form the cornerstone of a functioning society. They are listed in the diagram below:
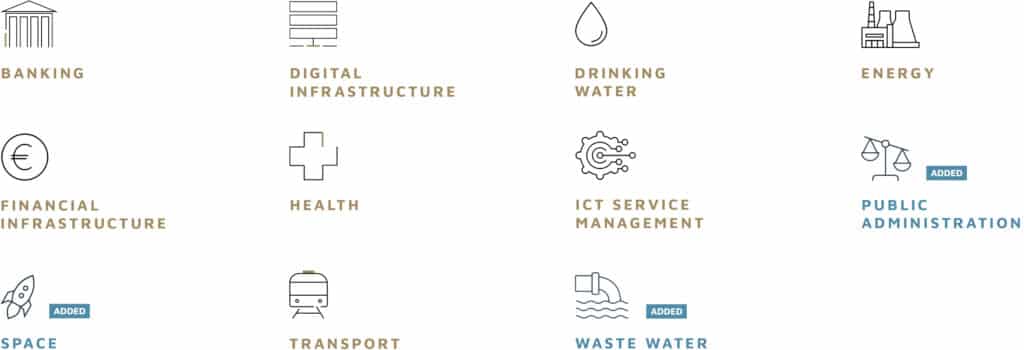
“Digital infrastructure” is a functionally broad sector that includes internet exchange point providers, DNS service providers, TLD name registries, cloud computing service providers, data center service providers, content delivery network providers, trust service providers, public communications network providers and electronic communications service providers.
“Energy” includes all main energy sources, including electricity production and distribution, district heating and cooling, oil production, refining, storage and stockholding, natural gas production, supply and distribution, hydrogen production, storage and transmission.
“ICT service management” includes B2B managed service providers and managed security service providers.
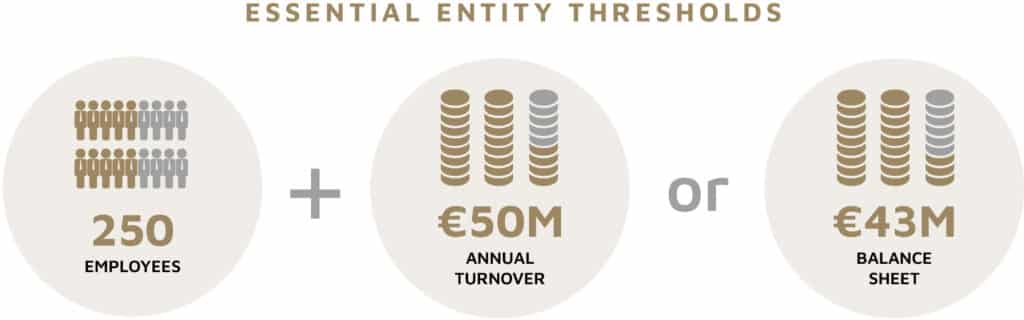
The NIS2 size threshold for an essential entity varies by sector, but the typical minimums are 250 employees and an annual turnover of 50 million Euros or a balance sheet of 43 million Euros. It is important to note that essential organizations that do not meet the size requirements of the ‘essential’ category are still deemed to be ‘important’ entities (see next section below).
Important entities
The list of entities defined as ‘important’ by the NIS2 directive has been greatly expanded in comparison to NIS1. In NIS2, the list of important entities includes a broad range of key manufacturing and service sectors.

“Durable goods manufacturing” is a broad category that includes medical device, computer, electronic, optical, electrical, machinery, vehicle, trailer and other transport equipment manufacturing.
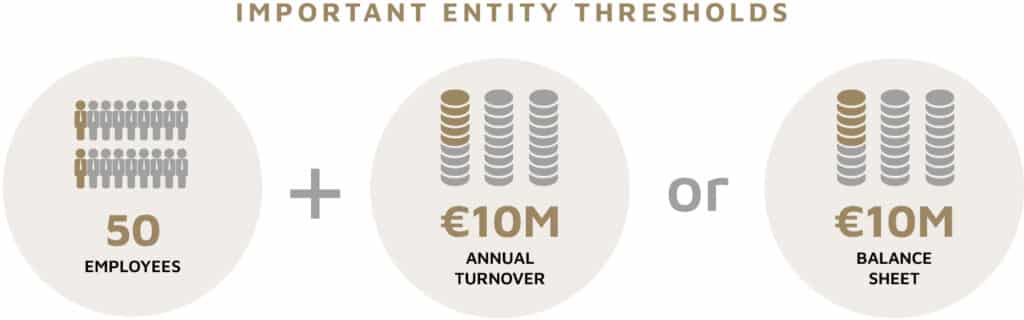
The NIS2 size threshold for important entities varies by sector, but typical minimums are 50 employees, and an annual turnover of 10 million Euros or a balance sheet of 10 million Euros.
Preparing for NIS2
Impacted organizations need to start now
Organizations that are classified as essential or important entities need to start preparing for NIS2 now because it will take time to implement the internal measures that NIS2 mandates. Below is a guideline on how to check and achieve readiness for specific NIS2 measures.
First step: a gap analysis
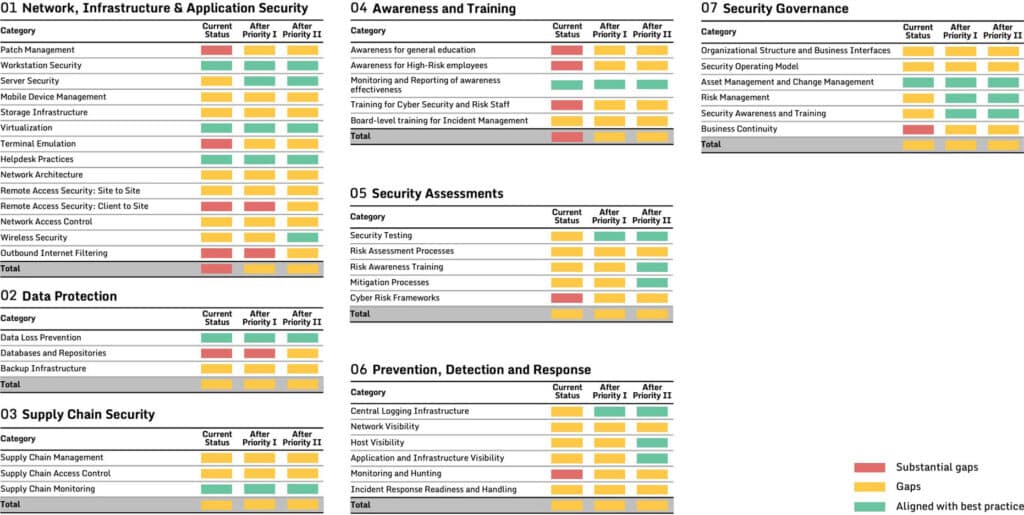
The requirement to perform a risk assessment and security policy review mandates that the organization perform a structured assessment of its current security posture and defensive capabilities in comparison to industry best-practices. A gap analysis should be the starting point of an organization’s NIS2 compliance journey.
One of the outputs should be a dashboard of the organization’s current cyber resilience levels, including strengths and security gaps that need to be closed.
Detailed recommendations are critical
An executive-level view needs to be complemented with detailed resilience enhancement initiatives that provide clear guidelines for the organization’s security implementation teams. Each enhancement initiative should describe in detail each recommendation and how it should be implemented.
Supply chain security and ongoing monitoring
The increasing digital integration between supply chain partners has made supply chain cyber security a crucial element of cyber resilience for many organizations. The EU recognized this and has made supply chain security a key mandate in NIS2.
Organizations that have a digital connection with supply chain partners need to widen the scope of their posture analysis to include those partners, regardless of whether those partners are located in the EU. That analysis should include a security roadmap with detailed, actionable and measurable recommendations that can be used to catalyze a structured and accelerated enhancement of supplier security and a reduction of supply chain risk.
The cyber posture and risk analysis that needs to be applied to the digital supply chain includes coverage of data storage and processing services, software, and any managed security services. The security posture and practices of supply chain partners need to be evaluated in comparison with industry best-practices.
A challenge that clients often describe is their lack of proactive monitoring of critical suppliers. This situation can undermine NIS2 compliance. It is critical to follow-up a supplier posture analysis and subsequent risk reduction program with ongoing monitoring to ensure that the improved situation is maintained.
Incident management and reporting
Incident handling is a core security measure that must be in place for NIS2 compliance. Incident handling, as defined in NIS2, includes any actions and procedures aiming to prevent, detect, analyse, contain, respond, and recover from an incident.
In practice, when an incident occurs an organization must work in parallel on a number of tracks to rapidly contain the incident, minimize the damage and simultaneously capture the data necessary to fulfill reporting requirements. In addition to technical and operational activities, executive-level crisis management is required during major incidents.
Incident reporting has a prominent emphasis in the standard, and in comparison to NIS1, NIS2 has even stricter incident reporting requirements. An organization that experiences a major cyber attack must provide an immediate warning to their country’s cyber security agency within 24 hours, and a detailed notification of the incident within 72 hours. The detailed notification needs to include an assessment of the impact of the incident on operations, end-customers, and supply chain partners. It also is preferred that the indicators of compromise be included in the report. Within 30 days, the organization must submit a final, detailed report about both the incident and the response.
Reporting is also required at the national level. Each EU country’s CSIRT (Computer Security Incident Response Team) must file a quarterly summary report to the European Union Agency for Cybersecurity (ENISA) about cyber incidents that occurred during the previous 3 months, using anonymized information. The ENISA also needs to report to the EU on a bi-yearly basis. The ultimate goal of the enhanced reporting requirements is to help organizations and member states learn from each other and benefit from the synergy of a collective approach to cyber security.
Leadership accountability
Organizations need to prepare a crisis management and business continuity plan. Under NIS2, executive leadership will be held accountable for any significant external impact of a breach. A crisis management and business continuity plan guides how executive and operational teams should react in a crisis.
To be ready for an NIS2 audit, the organization needs to review its cyber playbooks and budget time for an update or build-out prior to the NIS2 compliance date. Tabletop wargames are a highly effective way to stress-test crisis preparedness and should take place at the beginning of the organization’s NIS2 preparation timeline.
Adversarial simulations
NIS2 recognizes that cyber defenses and crisis preparedness need to be tested. Hands-on adversary simulations (red teaming) should be applied against the organization’s cyber defenses, replicating real threat-actor tactics, techniques, procedures that will likely be used by attackers against the organization. Security system gaps, misconfigurations, and exploitable vulnerabilities should be identified, and appropriate mitigations recommended.
Penalties
NIS2 mandates heavy fines and penalties in the event of a violation of Article 21 (Cybersecurity Risk-management Measures) or Article 23 (Reporting Obligations).
Essential entities are subject to administrative fines up to a maximum of at least EUR 10M or at least 2% of total worldwide annual turnover, whichever is higher. (‘At least’ refers to the fact that individual EU countries are allowed to set the maximums even higher).
Important entities are subject to administrative fines up to a maximum of at least EUR 7M, or at least 1.4% of the entity’s total annual worldwide turnover, whichever is higher.
Member states are also allowed to enact criminal penalties for infringements of NIS2, however such penalties are subject to the principle of ‘ne bis in idem’ which means that one shall not be punished twice for the same offense.
Suspension of product or service offerings can also be levied on an essential entity.

Sygnia can help accelerate achievement of NIS2 readiness
Sygnia works with companies across a wide range of verticals to proactively build their cyber resilience, regulatory compliance, and ability to respond and defeat attacks within their networks. Sygnia is the trusted advisor and service provider of technology and security teams, management and boards of leading organizations worldwide, including multiple Fortune 100 companies.
For more information on Sygnia’s NIS2 readiness services, please click on one of the contacts below.



By clicking Subscribe, I agree to the use of my personal data in accordance with Sygnia Privacy Policy. Sygnia will not sell, trade, lease, or rent your personal data to third parties.



