
Mitigation Advisory: Fortinet and Ivanti Exploitable Vulnerabilities
Protect your network against critical remote code execution vulnerabilities in Fortinet and Ivanti (formerly Pulse Secure) devices, now actively exploited in the wild.
Summary
A series of critical and exploitable vulnerabilities have been recently discovered within Fortinet and Ivanti products, requiring immediate attention. These vulnerabilities notably affect Fortinet FortiOS appliances, FortiGate SSL VPN, Ivanti (formerly Pulse Secure) Connect Secure, and Ivanti Policy Secure devices.
Network edge appliances, especially SSL VPNs, are a frequent and lucrative attack vector for adversaries. Attackers can exploit these vulnerabilities within Fortinet and Ivanti network edge appliances to gain network access and install malicious code, creating a backdoor that can be utilized in future attacks. Sygnia urges CISOs, and network and security teams to take immediate action to secure your network as the situation continues to develop.
Immediate action is imperative, as malicious actors are actively exploiting the recently disclosed vulnerabilities – as verified by CISA reports about Fortinet and Ivanti. Sygnia has analyzed these exploits, and is armed with effective mitigation strategies.
If you suspect that you are facing a potential breach, Sygnia’s team stands ready to be your trusted partner in remediation and recovery. Sygnia has faced down some of these specific vulnerabilities before, and many other similar ones, successfully assisting numerous clients in mitigating the impact of these vulnerabilities, and restoring clients to a robust security posture.
To learn more about Sygnia’s incident Response services, click here.
If you were impacted by this attack or are seeking guidance on how to prevent similar attacks, please contact us via email [email protected] or our 24 hotline +1-877-686-8680
Technical Details
Fortinet
Products Affected:
- FortiOS
- FortiProxy
- FortiPAM
- FortiSwitchManager
For affected versions, please refer to the vendor’s advisories listed below.
| CVE | CVSS Score | Vulnerability | Vendor’s Advisory |
| CVE-2024-21762 | 9.6 – Critical | Remote code execution – sslvpnd | FG-IR-24-015 |
| CVE-2024-23113 | 9.8 – Critical | Remote code execution – fgfmd | FG-IR-24-029 |
Mitigation:
- Identify all affected Fortinet appliances and products in the environment.
- If you are unable to immediately patch the affected appliances, it is advised to apply appropriate workarounds:
- For CVE-2024-21762 (sslvpnd), disabling SSL VPN will mitigate the risk, while preventing remote access from employees using this service.
- For CVE-2024-23113 (fgfmd), removing FGFM access for each interface will mitigate the risk. This will disable FortiManager discovery capabilitie.
- In any case, ensure to disable the features if they are not in active use, to reduce the general attack surface.
- Upgrade to a mitigated version according to the official Fortinet advisories, listed above.
- After upgrading and rebooting the appliances, FortiGate devices perform a system integrity check to search for files that have been tampered with. If there are any failures in the integrity check, a log is generated with ID 20234. It is advised to search for this event, and if tampering is identified, contact Sygnia for incident response support. For more information about this event, please see: https://docs.fortinet.com/document/fortigate/7.4.1/administration-guide/226732/real-time-file-system-integrity-checking
- In any case, conduct proactive monitoring and threat hunts within the environment to look for other indicators, including behavioral, of compromise.
Ivanti
Products Affected:
- Ivanti Connect Secure (formerly known as Pulse Connect Secure)
- Ivanti Policy Secure
- Ivanti Neurons for Zero Trust Access (ZTA) Gateways
For affected versions, please refer to the vendor’s advisories listed below.
| CVE | CVSS Score | Vulnerability | Vendor’s Advisory |
| CVE-2023-46805 | 8.2 – High | Authentication bypass | KB CVE-2023-46805 (Authentication Bypass) & CVE-2024-21887 (Command Injection) for Ivanti Connect Secure and Ivanti Policy Secure Gateways |
| CVE-2024-21887 | 9.1 – Critical | Command injection | |
| CVE-2024-21888 | 8.8 – High | Privilege escalation | |
| CVE-2024-21893 | 8.2 – High | Anonymous request forgery | |
| CVE-2024-22024 | 8.2 – High | Authentication bypass |
Mitigation:
- Identify all affected Ivanti products in the environment.
- Utilize Ivanti’s Integrity Assurance tool on each appliance. If the tool reports on any ‘mis-matched’ files (as seen in the screenshot below) or ‘newly detected files’, the appliance might be infected with malware. The tool can be found at https://forums.ivanti.com/s/article/KB44755
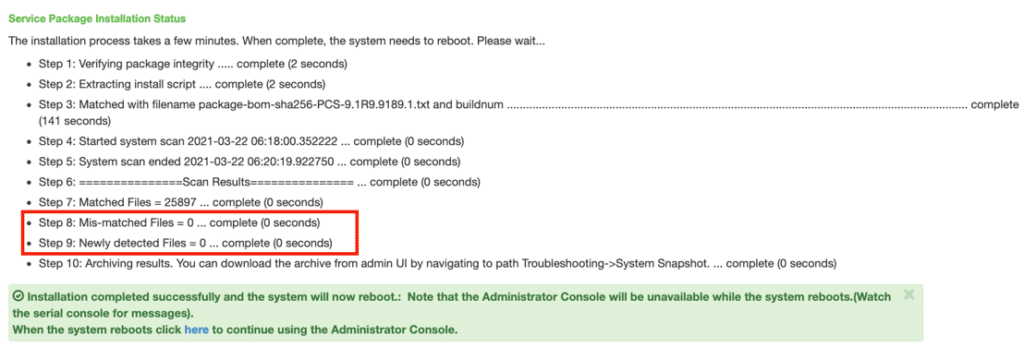
- If no files are detected, back up the appliances, and upgrade to the latest version as outlined in the official guidance: https://forums.ivanti.com/s/article/KB-CVE-2023-46805-Authentication-Bypass-CVE-2024-21887-Command-Injection-for-Ivanti-Connect-Secure-and-Ivanti-Policy-Secure-Gateways
- Please note that there have been unofficial reports in social media that functionality for SAML authentication may be negatively impacted after applying this upgrade.
- If file mismatches are detected, keep the appliances quarantined, as the appliances may have been exploited.
- Send a request to Ivanti customer support, and request decrypted images of the Ivanti appliances. Sygnia can assist with the analysis of the decrypted images.
- Conduct a factory reset of the appliances and restore the appliances with the specified versions. Please notice that factory reset erases any evidence usable for investigation and takes 3-4 hours.
- Rotate all stored credentials (e.g., API keys, certificates, admin password, local users). This may affect the Ivanti VPN’s performance and reliability unless the new credentials are properly synced with the dependent devices, services, and applications.
- In any case, conduct proactive monitoring and threat hunts within the environment to look for other indicators, including behavioral, of compromise.
To learn more about Sygnia’s incident Response services, click here.
If you were impacted by this attack or are seeking guidance on how to prevent similar attacks, please contact us via email [email protected] or our 24 hotline +1-877-686-8680

By clicking Subscribe, I agree to the use of my personal data in accordance with Sygnia Privacy Policy. Sygnia will not sell, trade, lease, or rent your personal data to third parties.



