
Building Cyber Readiness: 5 Traits of the World’s Most Cyber-Ready Organizations
The most dangerous cyber attackers have something in common: they are tenacious at their craft and dogged in their determination to find and exploit security weaknesses.
Defenders of the world’s most cyber-ready organizations match this intensity and have what it takes to beat adversaries at their game. For them, cyber readiness isn’t a static state; it’s a continuum of vigilance in which they know where they stand, prepare for anything, simulate attacks to test and optimize security measures, detect and eliminate threats quickly, and respond and recover swiftly to minimize business impact.

Exploring cyber-ready organizations’ experiences and best practices across these five defining areas can help inform your strategy along the cyber security journey so you can proactively build cyber resilience and quickly defeat attacks in your network.
5 Traits of Cyber-Ready Organizations
1. Cyber-ready organizations KNOW where they stand
“Cyber-ready organizations hold the upper hand by knowing how cyber attacks will manifest in their environment,” says Yossi Torati, Director of Enterprise Security at Sygnia. “They may not know when an attack will happen, but they do know where and how it could materialize – and its potential business impact.”
Truly understanding your organization’s ever-evolving cyber posture and risk profile hinges on your ability to see clearly across your digital landscape. In-depth cyber posture assessments can expand your view and answer these critical questions:
What matters most? Your answer may be obvious, such as maintaining business continuity, safeguarding intellectual property, or ensuring compliance with data protection regulations. However, truly driving your security plan to achieve this often requires a deep, systematic analysis of your IT environment, assets, organizational structure, and business context. Defining your organization’s most critical assets and processes and translating that to prioritize your security plan is foundational to enhancing cyber readiness.
What risks do I face? Keeping a pulse on the latest media reports and industry databases is essential, but adversaries don’t wait for the MITRE ATT&CK Framework or NIST NVD. From evolving AI-fueled threats, new attack vectors in Azure AD Connect, surging business email compromise (BEC) incidents, emerging ransomware groups, and everything in between, you need insights on real-world attack patterns and techniques before they’re published to bolster your cyber posture and prioritize defense strategies. Knowing what you don’t know – and where and how to acquire this missing information – is critical.
How resilient is my tech stack? Surfacing areas of weakness, such as security system misconfigurations, design flaws, and exploitable vulnerabilities, enables a deeper understanding of how adversaries will use them against you. Posture assessments can also identify technical drift due to a constantly changing digital landscape, ensuring your security systems are continuously optimized and working as they should to stop threats and deliver ROI.
How will organizational transformation impact my risk profile? You must understand your cyber resilience today and how changes to your environment will affect your posture over time. For instance, as your organization migrates to the cloud, each new initiative introduces attack vectors and necessitates new identity and access management (IAM) controls, network segmentation modifications, compliance considerations, enhanced visibility requirements, and specialized knowledge and skills. Perhaps you’re approaching a significant company milestone, such as a merger or acquisition. Understanding your target company’s cyber security posture is critical to securing your collective environment and avoiding unexpected financial expenses, legal suits, and reputational damage.

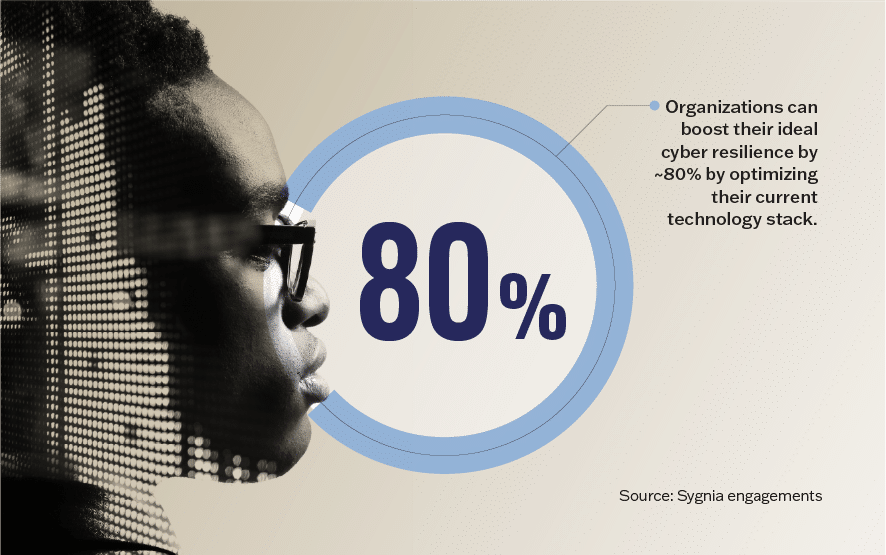
What needs to be done – in what priority order – to bolster your cyber posture? With a keen understanding of your cyber security posture, you can quickly close critical gaps and focus on creating a long-term, strategic roadmap for high-impact improvements. A strategic partner can guide you through this process while helping you maximize investments. Contrary to popular belief, and based on Sygnia experts’ experience, organizations can boost their ideal cyber resilience by approximately 80% by optimizing their current technology stack.
2. Cyber-ready organizations PREPARE so they are ready for anything
Cyber-ready organizations don’t wait for a hair-on-fire crisis to make plans – that’s when stress levels skyrocket, communication breaks down and, as Adam Finkelstein, Sygnia’s Senior Vice President, Global Client Leadership sees often, “it will likely be on a Saturday night when you’re least expecting it.”
“Every organization will be attacked. Don’t wait for your ‘when’ to prepare,” he continues.
Once your plan is in place, the work isn’t over. “Preparation is about building muscle memory as an organization, like an Olympian who trains for years for that one defining moment,” says Finkelstein. “The commitment to practice at every level is what enables you to be ready for anything.”
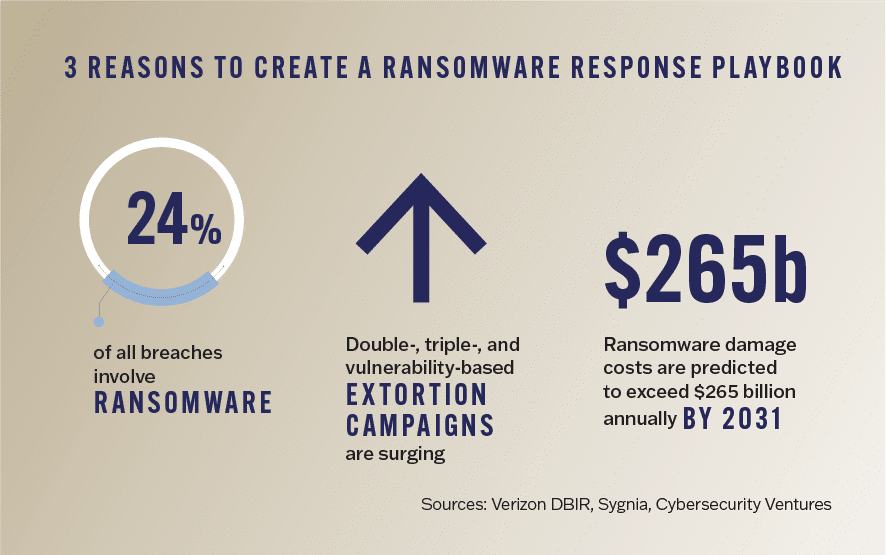
Recent attack trends underscore the need for proactive planning and a fit-for-purpose incident response strategy. After shattering records in 2023, ransomware groups continue their shift from data encryption to exfiltration, upping the ante with double- and triple-extortion schemes to boost profits. They’re also zeroing in on zero-day vulnerabilities to execute MOVEit-inspired mass exploits, stepping up supply chain and third-party attacks, and leaning heavily on initial access brokers to get inside networks and bypass existing authentication mechanisms.
Such attacks are inevitable, but $4.45 million in losses – the average data breach cost today – is not.
A robust and well-practiced plan provides order and structure so you can be ready with the right team and flows to stop attacks before they stop you.
“After a cyber incident, there’s an instinct to adapt plans to fight the war that just passed,” says Finkelstein. “This is important, but only preparing for what you know is a failure of imagination. Cyber attackers continually iterate, adapt, and advance, so you must, too. Cyber readiness is active vigilance – always forward looking and future leaning.”
A tech-agnostic partner with unbiased perspectives and real-world expertise can help you design a highly customized yet flexible plan that empowers your organization to be cyber ready and prevail in times of crisis, no matter the challenge.
An ounce of prevention is truly worth a pound of cure. Gartner predicts that by 2026, organizations investing at least 20% of their security funds in resilience and flexible design programs will cut total recovery time in half when a large blast attack occurs.

3. Cyber-ready organizations SIMULATE attacks to test and optimize security measures
History –and experience – has taught us that battle-testing your plan is the only way to make it great and weave it into the fabric of the company.
Chris Crummey, Director, Executive and Board Cyber Services at Sygnia, often draws on the “Miracle on the Hudson” to illustrate how crucial simulations are for testing incident response plans and building cyber readiness.
Every flight has one thing in common: the safety briefing. But on January 15, 2009, US Airways Flight 1549 struck a flock of birds shortly after leaving LaGuardia Airport, losing all engine power. Thanks to the experienced, quick-thinking flight crew, the plane landed safely in the Hudson River, and all survived. Yet out of the 155 individuals on board, only four had their life vests, and just one wore it correctly. This is why corporations need to continue to conduct simulations to increase the confidence of the roles and responsibilities of the primary stakeholders.

“Attack simulations take your organization through its worst possible day, so you can understand what great looks like,” Crummey says. “Putting your capabilities under live fire fuels risk-based decision-making, helping you tackle difficult questions with limited information such as ‘Would we pay a ransom or not?’ or ‘How do we determine materiality and meet stringent SEC reporting requirements after an incident?’ Simulations also uncover gaps and strengths so you can strategically optimize security measures. Most importantly, they help align stakeholders, ensuring your cyber response is a full business response,” he continues.
The widely embraced 70:20:10 learning and development model suggests that 70% of human learning is experiential. Corroborating studies show that active learning methods, such as ideation, immersion, and gamification, can significantly enhance knowledge retention and competency. Hands-on simulations with technical teams, such as intensive red-teaming and purple-teaming, help bridge the gap between theory and practice. Similarly, tabletop wargames help prepare executives and security leadership for high-stakes crises.
Independent testing teams bring objectivity and a sharp rigor of thinking, pressure-tested in real-world environments. By providing a safe and controlled environment for your people to push themselves and sharpen skills, procedural knowledge becomes instinct, enabling faster response and recovery when an actual incident occurs.
An outside look at your incident response strategy, architecture, and operating model can also uncover inherent biases and deficiencies that impede efforts. For instance, virtualization technology is often overlooked in defensive plans and tests. However, Sygnia has observed a spike in ransomware attacks utilizing ESXi servers in recent months, which suggests that adversaries are using these blind spots to their advantage.
Attack simulations aren’t always comfortable, but they’re integral to building cyber readiness and elevating your capabilities against real-life threats.

4. Cyber-ready organizations DETECT and eliminate threats quickly
An attacker is hiding in your network right now. They have full access to your most sensitive assets and systems, can bypass security defenses, and hide by impersonating real users. Do you have the skills, tools, and forensic data insights to find them before it’s too late?
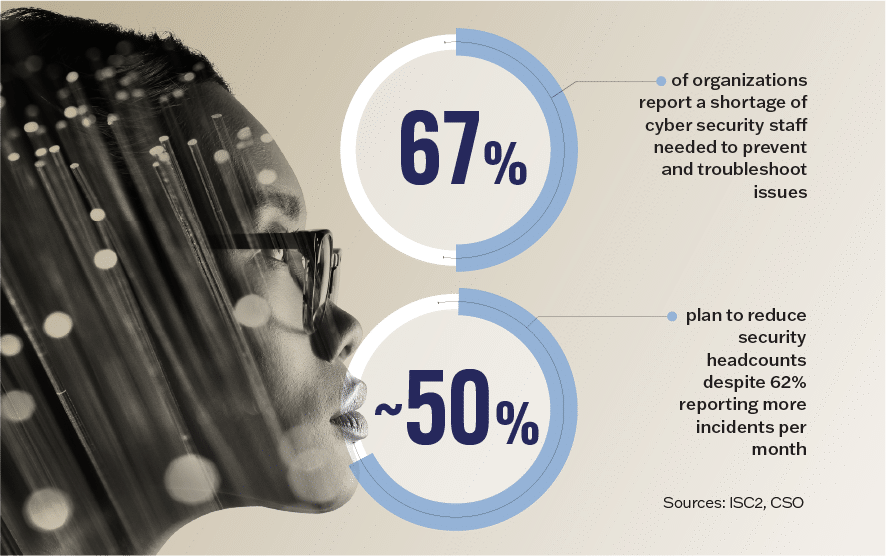
The infamous SolarWinds breach – a sophisticated supply chain attack that infiltrated the company’s software and impacted numerous government agencies and Fortune 500 companies – forced everyone to consider this question and their far-reaching third-party dependencies. Yet more than three years later, identifying a breach still takes an average of 204 days. It’s not for a lack of threat data. In fact, most under-resourced security teams are drowning in alerts.
With time on their side, adversaries continue to evolve, adopting stealthier methods to evade detection such as:
- Dynamic-link library (DLL) side-loading, which places a malicious DLL file on a system so a legitimate program automatically loads it.
- Web shell attacks that establish backdoors in targeted web applications.
- Fileless malware attacks that employ native software tools for malicious purposes and do not require the attacker to install code. LOLBins – short for living off-the-land binaries – is an increasingly popular fileless attack method.
- Open-source software abuse, utilizing widely used tools for tunneling, exfiltration, and remote connection.
Cyber-ready organizations recognize that shifting the scales in their favor requires a holistic security approach, embracing the best talent and technology to enhance visibility, combat ever-evolving threats, and contain attacks. This is where managed extended detection and response (MXDR) plays a critical role in the fight against cybercrime. Managed XDR is super-charged by artificial intelligence and machine learning to automate manual security tasks, enable deeper insights, and accelerate remediation efforts.
According to Gartner, 57% of organizations resolve security threats faster after implementing an XDR strategy.
Many organizations are turning to fully managed XDR services that unify threat monitoring, detection, and response functions while enabling cross-enterprise visibility – of networks, cloud, OT, endpoints, and everything else – through a single pane of glass. With this approach, once an alert is triggered, every data type from all organizational data sources is automatically correlated into one unified, contextualized alert, driving unmatched breadth and depth of investigation.
But that’s just the start. “In security operations, context is everything – and it’s key to building cyber readiness,” says Sygnia Product Manager Keren Katz. “Threat data truly becomes actionable when it’s paired with expert mitigation recommendations that continuously integrate real-world incident response data on emerging threats, are custom-made for your environment, and are seamlessly delivered and consumed.”
The synergy of global cyber expertise and advanced managed XDR fast-tracks forensic collection and enables a seamless transition from monitoring to response – so you can stop attacks faster. The most effective MXDR offerings feature out-of-the-box integrations for expedited protection and time to value. And with round-the-clock monitoring and support, hiring, training, and maintaining an in-house SOC team is unnecessary.
On your cyber security journey, a forward-thinking partner who fuses technical excellence with frontline expertise can empower your team to shorten mean time to detect (MTTD) and mean time to respond (MTTR) to known and nascent threats and establish continuous high assurance and vigilance – all while reducing internal security burden and overhead.

5. Cyber-ready organizations spring into action to RESPOND & RECOVER swiftly
You’ve been attacked. Now what? The decisions you make and the steps that you take in the first few hours are critical as you work to resolve and recover with as little business impact as possible.
The clock is ticking, and every minute counts because “attackers are in the pressure business,” says Ori Porag, an Incident Response Expert at Sygnia. “They often turn up the heat by setting a clock and threatening to take action, such as publishing files or losing the encryption key, if demands aren’t met on their schedule.”
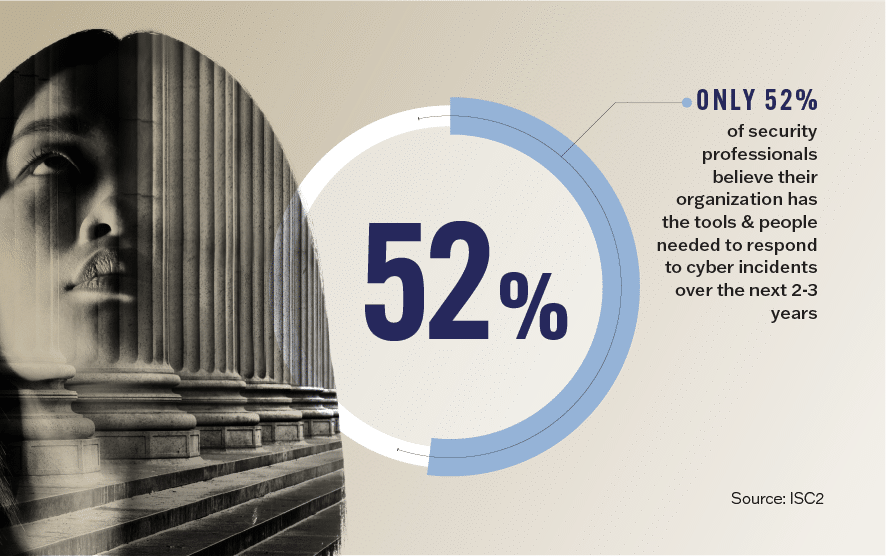
You have prepared for this moment. You fully understand your cyber posture. You’re prepared with a robust, rigorously tested plan, and everyone clearly understands their roles and responsibilities. You detected the threat quickly with a combat-proven understanding of the adversarial mindset. You are ready. But right now, many things must happen all at once. If you’re like many organizations out there, you don’t have all the in-house team members and tools you need to swiftly respond and defeat the attack and ensure that your organization experiences as little business impact as possible.
This is where a seasoned incident response team is essential. While you remain focused and on plan, they can manage multiple parallel workstreams to accelerate incident resolution, including:
- Crisis management, expertly guiding executive leadership through the crisis, communicating effectively with all stakeholders, and supporting legal, regulatory, public relations, and internal efforts throughout the ordeal.
- Containment, quickly ensuring that unaffected areas of your environment remain untouched and out of reach from attackers.
- Skilled triage and investigation, identifying the initial point of entry, the attack kill chain and scope of the compromise, the attacker’s tools and tactics, and the current threat level.
- Tactical negotiation, serving as a liaison between you and the attacker. This can help you gain valuable time and shed light on the enemy’s goals, allowing you to see through their smokescreen and focus your investigation and response.

- Day-one remediation efforts, using “secure island” environments to accelerate time to recovery and get you back in business faster.
- Tailored threat monitoring, ensuring additional malicious activities and re-entry attempts are detected and blocked immediately.
A highly orchestrated incident response approach has enabled some of the world’s largest organizations to recover from major attacks successfully. Consider the global manufacturing company that fully recovered from a paralyzing PYSA ransomware attack within two weeks of initial compromise. And the major telecom provider that shut down a corporate espionage campaign that had besieged them for half a decade. Finally, the leading cryptocurrency exchange caught in the crosshairs of a nation-state attack that overhauled its security practices and now serves as a model for other financial organizations in this increasingly targeted space.
Whether you’re facing a criminal enterprise, a state-sponsored attacker, or a malicious insider, having a trusted advisor beside you – in times of crisis and calm – can give you the confidence to navigate the high-stakes cyber challenge and emerge even stronger.
Are you cyber ready?
Cyber-ready organizations are those who are best prepared for whatever may challenge their cyber security. It defines those who proactively solidify cyber defenses, those who have developed relationships with partners who can help them seamlessly manage the impact of an attack, and those who maintain an active state of vigilance and preparation.
To be cyber ready, you can’t rest so neither do we. We don’t expect two attackers to act precisely the same. We don’t assume that yesterday’s attack will look like tomorrow’s. We don’t fall back on templatized approaches or automatically default to standard solutions. And we don’t stop until we’ve found a way.
As the foremost global cyber readiness and response team, Sygnia applies creative approaches and battle-tested solutions to help your organization beat attackers and stay secure. From executive-level strategic guidance to on-the-ground technical expertise, everything we do is in steadfast service to your best defense. We’re in until the threat is out.
Learn how Sygnia can support each phase of your company’s security journey, spanning assessment, preparation, testing, detection, and incident response, so you can be unstoppable in the face of cyber threats. To explore frontline threat insights, download the newly released 2024 Sygnia Annual Field Report.

By clicking Subscribe, I agree to the use of my personal data in accordance with Sygnia Privacy Policy. Sygnia will not sell, trade, lease, or rent your personal data to third parties.



